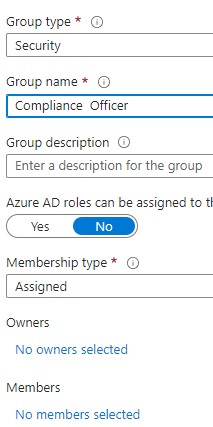
On January 30th, 2021, Microsoft discontinued the capability for administrators to customise the refresh interval of an ID or SAML token. Instead, they introduced a novel functionality within conditional access known as “sign-in frequency,” which governs the refresh and session token lifetime policy properties.
Properties governing the duration of refresh and session tokens’ lifetimes
Ref: https://learn.microsoft.com/en-us/entra/identity-platform/configurable-token-lifetimes
| roperty | Policy property string | Affects | Default |
|---|---|---|---|
| Refresh Token Max Inactive Time | MaxInactiveTime | Refresh tokens | 90 days |
| Single-Factor Refresh Token Max Age | MaxAgeSingleFactor | Refresh tokens (for any users) | Until-revoked |
| Multi-Factor Refresh Token Max Age | MaxAgeMultiFactor | Refresh tokens (for any users) | Until-revoked |
| Single-Factor Session Token Max Age | MaxAgeSessionSingleFactor | Session tokens (persistent and non-persistent) | Until-revoked |
| Multi-Factor Session Token Max Age | MaxAgeSessionMultiFactor | Session tokens (persistent and non-persistent) | Until-revoked |
Conditional Access Options for Sign in Frequency
Microsoft has enhanced Conditional Access by introducing a new feature: sign-in frequency. The default options for sign-in frequency include hours and days, with a minimum setting of 1 hour and 1 day.

This option was a very welcome addition to the Coitional Access, session control options. Zero Trust , explained simply , ‘always assume breach’ on LAN or WAN.
However when working with an organisation on a cloud transformation journey that is moving from Microsoft Office 2010 \ 2013 , Exchange 2010, 2013. Too much change can become counter productive for an organisation. It is a black art finding the balance between security and productivity. Obviously security must always win.
The inclusion of this feature was a significant enhancement to Conditional Access session control options. In simple terms, Zero Trust advocates ‘always assume breach,’ whether on LAN or WAN. Nevertheless, when collaborating with an organisation undergoing a cloud transformation from Microsoft Office 2010/2013 and Exchange 2010/2013, excessive changes can potentially hinder productivity. Striking the right balance between security and productivity becomes a delicate task, with the clear understanding that security should always take precedence.
Require reauthentication every time
| Require user reauthentication during Intune device enrolment, regardless of their current MFA status. |
| Require user reauthentication for risky users with the require password change grant control. |
| Require user reauthentication for risky sign-ins with the require multifactor authentication grant control. |
There’s an additional scenario not covered in the mentioned Microsoft article—when an organisation establishes a new authentication context.


The crucial element in the depicted image is the ID of the Authentication Context policy. This ID can be allocated to critical SharePoint Online sites such as Finance, HR, Board of Management, ensuring that members of these sites are consistently prompted for authentication. This mitigates the risk associated with scheduled sign-in frequencies of 1 hour and beyond.
An hour is a significant duration, particularly in a scenario where an identity has been compromised. In just 5 minutes, a malicious actor who has compromised an organisation’s identity can swiftly pilfer intellectual and valuable information.
Summary
- The current sign-in frequency control, set at a minimum of 1 hour or a specified number of days, is effective for all SAAS applications integrated with Microsoft Azure AD.
. - For additional assistance with the mentioned items, feel free to reach out to me on LinkedIn: https://www.linkedin.com/in/seanofarrelll/
Configurable token lifetimes in the Microsoft Entra ID (Preview)
Ref: https://learn.microsoft.com/en-us/entra/identity-platform/configurable-token-lifetimes
Microsoft introduced a preview version for managing token lifetimes in Microsoft Entra ID on October 31, 2023. I haven’t had an opportunity to test it yet. Administrators lost the ability to configure refresh and session token lifetimes on January 30, 2021, and Microsoft hasn’t reinstated this capability for administrators since then. While it’s expected to function seamlessly with Microsoft applications integrated with Microsoft Entra ID, extensive testing is needed for the multitude of SAAS applications integrated with Microsoft Entra ID. Additionally, please be aware that this feature is currently in preview